Remote employees are in a conundrum when it comes to data security. While you might be able to protect data stored locally on your company’s in-house network, securing data in use by employees while out of the office is another matter entirely. How can you guarantee that your business is protecting its data and other sensitive resources from prying eyes?
Attend IT Blog
How often does your business find that it’s struggling with new technology implementation, either on the software side of the house or on the hardware side? Have you considered that the cloud provides powerful solutions to your business’ woes in the form of virtualization? With the right resources at your disposal, you can use virtualization to create incredible opportunities to improve operations for your business and make it more secure and flexible in the process.
Encryption stands as a formidable shield for businesses, fortifying their security architecture. While often discussed in VPN contexts, its significance in securing email solutions cannot be overstated. Why is email encryption indispensable for businesses of all sizes? Let's explore.
The cloud has become a go-to resource when businesses are trying to find and consistently depend on digital tools that otherwise would be out of their price range. One cloud issue that isn’t often mentioned in the course of choosing computing resources is cloud waste. Cloud waste refers to the inefficient or unnecessary consumption of cloud computing resources, leading to higher costs without delivering corresponding value. This month, we will look at some of the impacts of cloud waste and how to avoid it as much as possible.
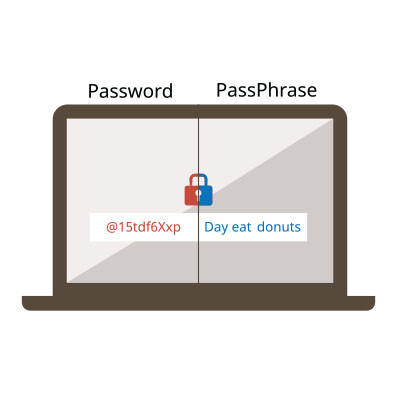
Securing your accounts against unauthorized access begins with the implementation of a strong password. It's crucial to recognize that not all passwords offer the same level of protection. Here are five essential guidelines to ensure the security of your accounts.